top of page

The Cyber Security Blog
Cyber Attack's, Malware, CVE's and more.


Analysis of an Intrusion Campaign Targeting Telco and BPO Companies
In this attack campaign, the adversary demonstrates persistence in trying to gain access to victim environments and performs constant,...
Dec 6, 20221 min read


Cranefly: Threat Actor Uses Previously Unseen Techniques and Tools in Stealthy Campaign
Symantec, by Broadcom Software, has discovered a previously undocumented dropper that is being used to install a new backdoor and other...
Dec 6, 20221 min read


Blowing Cobalt Strike Out of the Water With Memory Analysis
Cobalt Strike is a clear example of the type of evasive malware that has been a thorn in the side of detection engines for many years. It...
Dec 6, 20221 min read


LockBit 3.0 attacks and leaks reveal wormable capabilities and tooling
LockBit 3.0 attacks and leaks reveal a number of similarities between the latest generation of the ransomware and the BlackMatter...
Dec 1, 20221 min read


DUCKTAIL: An infostealer targeting Facebook Business accounts
A report has been published by cybersecurity firm, WithSecure Intelligence, on an operation that targets individuals and businesses that...
Nov 25, 20221 min read

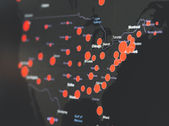
Aggressive Qakbot Campaign and the Black Basta Ransomware Group Targeting U.S. Companies
Cybereason’s global security team is investigating a potentially widespread ransomware campaign run by the Black Basta ransomware group,...
Nov 24, 20221 min read

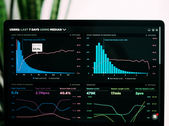
RobinBot – A new type of DDoS botnet in rapid expansion
In early November 2022, Qianxin Threat Intelligence Center detected an incident with malicious samples from unknown families. The...
Nov 23, 20221 min read

ViperSoftX: Hiding in System Logs and Spreading VenomSoftX
This multi-stage stealer exhibits interesting hiding capabilities, concealed as small PowerShell scripts on a single line in the middle...
Nov 23, 20221 min read


Nighthawk Pentest Tool
Nighthawk is an advanced C2 framework intended for red team operations through commercial licensing. Proofpoint researchers observed...
Nov 23, 20221 min read


Email Cyberattacks on Arab Countries Rise in Lead to Global Football Tournament
Global eyes are soon to be turned to the first global football tournament to be held in the Arab world kicking off on November 20, but...
Nov 22, 20221 min read


Aurora: a rising stealer flying under the radar
An investigation by security firm SEKOIA.IO into the activity of Aurora botnets has found that the malware is being used by a growing...
Nov 22, 20221 min read


Earth Preta Spear-Phishing Governments Worldwide
Trendmicro has been monitoring a wave of spear-phishing attacks targeting the government, academic, foundations, and research sectors...
Nov 22, 20221 min read


AXLocker, Octocrypt, and Alice: Leading a new wave of Ransomware Campaigns
Ransomware is one of the most critical cybersecurity problems on the internet and possibly the most powerful form of cybercrime plaguing...
Nov 18, 20221 min read


Technical Analysis of the RedLine Stealer
RedLine is an information stealer which operates on a MaaS (malware-as-a-service) model. This stealer is available on underground forums,...
Nov 18, 20221 min read


Reconstructing the last activities of Royal Ransomware
Royal Ransomware group started its malicious activities since January, with other ransomware payloads. They started their malicious...
Nov 18, 20221 min read


New RapperBot Campaign – We Know What You Bruting for this Time
After FortiGuard Labs reported on RapperBot in our previous article titled So RapperBot, What Ya Bruting For? in August 2022, there was a...
Nov 18, 20221 min read


Hack the Real Box: APT41’s New Subgroup Earth Longzhi
In this entry, we reveal two campaigns by Earth Longzhi from 2020 to 2022 and introduce some of the group’s arsenal in these campaigns....
Nov 11, 20221 min read


New “Prestige” ransomware impacts organizations in Ukraine and Poland
The Microsoft Threat Intelligence Center (MSTIC) has identified evidence of a novel ransomware campaign targeting organizations in the...
Nov 11, 20221 min read


Cranefly: Threat Actor Uses Previously Unseen Techniques and Tools in Stealthy Campaign
Symantec researchers have discovered a novel technique of reading commands from IIS logs to install backdoors and other tools in a...
Oct 31, 20221 min read


Raspberry Robin worm part of larger ecosystem facilitating pre-ransomware activity
Microsoft has discovered recent activity indicating that the Raspberry Robin worm is part of a complex and interconnected malware...
Oct 31, 20221 min read
bottom of page
